This morning I was confronted with an image. The image wasn’t the unsettling part, it was the part that the image did not give. You see, I got my first smart-card in 1991 by Unilever. They already had smart-card security when it was a myth at best.

Now consider the set-up above. This level of card cloning can now be done by a high schooler. And people think that this level of protection works? How quaint.
So my old noggin started to mull things over, we need to upgrade this stuff by a lot. I know all the people will state that this isn’t needed. But when insurance companies catch on that people are cutting corners the premium goes up by a lot. Now, my idea might not be the best solution, but I leave this to the ACTUAL cyber boys to mull this idea into something workable.
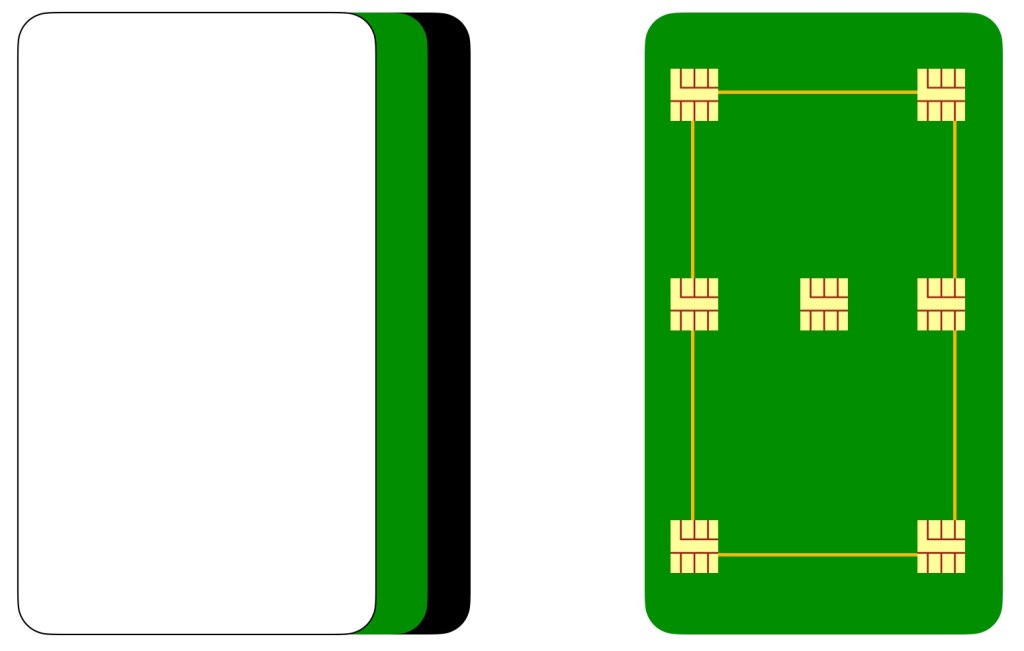
In my view the smart-card has 3 layers, the lowest layer is an RFID shield, this makes scanning the cards really hard, the middle layer is the circuitboard and the top layer is the plastic layer. Now the circuitboard can have 7 nano sims, but only a minimum of two are required. You see, all that cheap corner stuff is done for. The 6 sim locations are connected through printed circuitry, the one part a hacker cannot copy or clone. As such these sims become part of a non-repudiation process. And as they are specifically created for each client, you have 64 options right from the start and when you consider that each nano sim and the circuitry adds a few thousand combinations we can safely say that these hackers stop being a problem.
The centre sim is where specifics are programmed on site (hotel, corporation HR), the other one, or up to 3 other ones are SPECIFIC to that client. Yes, it could all fit ONE sim, but that is where people get into trouble and cyber criminals will have a field day.
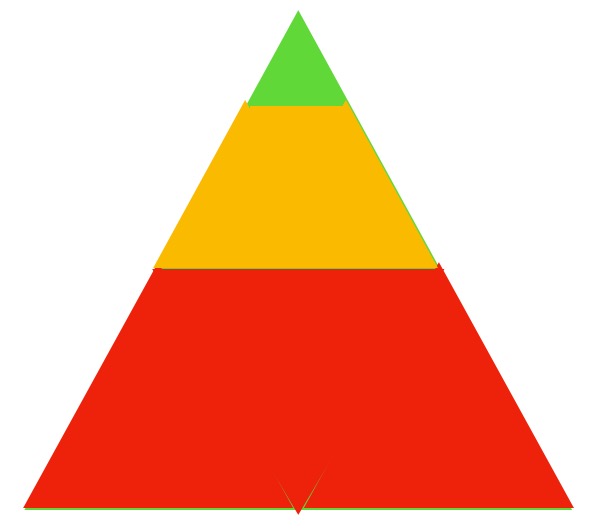
You see, what we do is raise the threshold. The image below gives the side I was after.
The lower part are the wannabe hackers, simple thieves and so on, that is a little over 50% of the lot and they are taken out of the equation completely. They lack the resources to make it work. The yellow are partial threats, these are the high end hackers. They are driven to results and finance, so if the goal is not the required need, it is left alone. That doesn’t make them a non-issue, but unless they have something really interesting to gain, they aren’t interested. The green ones are the remaining threats. People with government access, or serious funds. We have now removed a little over 90% of the threat that was in existence. You think and insurance company having to pay out millions upon millions will try to avoid having to pay at all. We can come with all the usual culprits, but that is not where it is at. Consider that a player like Northrop Grumman needs to keep their IP safe, the first stage is non-repudiation. That person and that person alone could have done this and a cloned card makes that part near impossible. In the end some will always have access, but when we can remove 90% from the equation, that part matters and it matters a lot. So that is what I was mulling over and this idea came to the top. Perhaps not everyone’s cup of tea, but that is not my concern. I had another idea, number 4 (or 5) this week alone and now I will snore like a sawmill, it is Wednesday here now.
Enjoy the day.