That is what I face at times. I get that my ‘idea’ of safety is a little overdrawn, but I have seen the stupidity of greed driven and how those seeking the stupid and greedy are willing to exploit that. I am of course referring to the really organised criminals (criminals with Filofaxes). That is the expected setting and on February 11th 2024 I wrote ‘Don’t take my word’ (at https://lawlordtobe.com/2024/02/11/dont-take-my-word/) I was considering the danger that a place like Funnel was presenting itself to be. And the presented advertising (a lot of it on LinkedIn)
showed a setting that I feared and guess what? I was partially right. I was right because that side was exploited and I was wrong as it was not Funnel who gave the setting. It was a place called Mixpanel where we see “more than 200 million premium users that their data may have been exposed when hackers breached third-party analytics provider Mixpanel” and last month we were given ‘Data breach at OpenAI through analytics provider Mixpanel platform’, which was seen (at https://securitybrief.com.au/story/data-breach-at-openai-through-analytics-provider-mixpanel-platform) you can wallow as much as you like that I was wrong, but that another platform provider is the first to fall, does not mean that I was wrong. The setting of ‘ease’ safety which they called “Hey marketer, tired of wasting time downloading and cleaning data from all your advertising platforms? It’s time to meet
Funnel. Save time, improve performance, get better insights with Funnel.” As I personally see it ‘tired of downloading’ should be seen as ‘safety towards your data’ and “cleaning data” often implies “validating and verifying the data you are using”, so if there are people that are thinking I am a proverbial shit bucket, consider the image below.
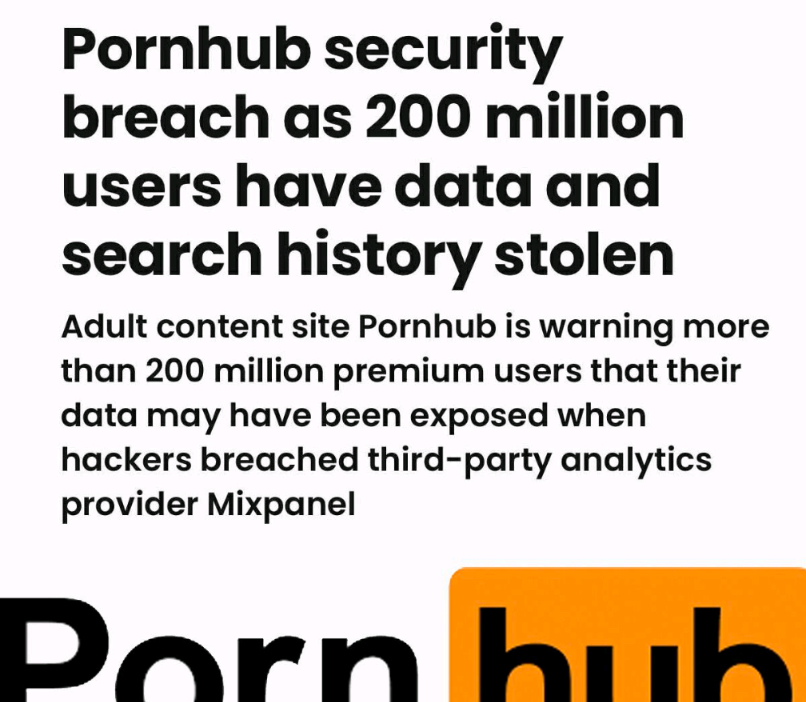
Where we see that in the proverbial instant. That resulted in the loss of some “200 million users have data and search history stolen” and yes, the 200 million records could see the setting that these 200,000,000 million users will get phased and the companies they optionally worked for too. That is the larger setting of being lazy, or being contemplated towards the security they never really had. Why did they not have that security? Because certain settings negate safeties that are and as I see it, Mixpanel who by the opinion of some is seen as “a product analytics platform that helps businesses track user interactions on their websites and apps to understand behavior, improve products, and drive growth” and as I see it, it is driving growth for the really organised criminals and now as we see (at https://securitybrief.com.au/story/data-breach-at-openai-through-analytics-provider-mixpanel-platform) we are given “The incident was related to unauthorised access to a dataset within Mixpanel’s systems. OpenAI reported that an attacker exported data containing certain identifiable information of API account users. Details potentially exposed included names provided on API accounts, email addresses, approximate location information, operating system and browser details, referring websites, and the organisation or user IDs linked to the API accounts. OpenAI emphasised that no chat logs, API requests, passwords, keys, payment details or sensitive identification documents were accessed. The data breach affected only information collected for analytics purposes through Mixpanel.” I get that this is the OpenAi answer, but it seems shallow, short, and perhaps that is all it is, but there is a second setting. Either the ‘provider’ who sounds like Promohub is giving us a larger pool of users, or some clever person might be insightful enough to combine the data of two pools of data and see what could be linked, because any person whose ‘shortcomings’ are exposed will seek other ways to hide the ‘shortfall’ and that is exactly what criminals are banking on. OK, this is speculation but if I had these two pools of data, I the first thing I would do is to seek a common ground (like an email address) and see what else I can find. This is how I found the weakness towards the Pentagon using the HOP+1 solution (which is wrongly analyzed by what some call AI) it was the first thing I did last month. And now again I am right. To be clear, the article on Funnel was about Funnel and as far as I know it was never transgressed upon. It was merely a fear I held and the fear was shown correctly at Mixpanel, not Funnel.
So whilst OpenAI correctly gives us “Information potentially accessed through Mixpanel may expose users to an increased risk of phishing or social engineering attempts.
Names, email addresses, and user identifiers were among the details exposed. OpenAI has advised all customers and users to remain vigilant for any suspicious or unsolicited communications that could be related to this incident. The company reiterated that it does not request sensitive information such as passwords, API keys, or verification codes via email, text, or chat. Users have also been encouraged to enable multi-factor authentication as an additional protective measure for their accounts.”
And why am I now up in arms? Because I got the word through another source relating to another vendor and that implies that there are at least three data sources exposed and those with connected data will be at risk. As such there is little risk for OpenAI and its users if it is used correctly, but when is that the case and it falls back on the users, not on OpenAI. There is an old premise that I usually phrase. If 5 vendors have a 10% loss, the customer is at risk of losing 50% and that is what the danger is here. And when this is applied to 200,000,000 users, the losses could be close to astronomical.
Now we can argue that there is no such risk, but that answer is coming mostly from people claiming to have no P#Hub account. Do they? I cannot tell, but they know if they have or not. And to also be clear, there is absolutely nothing wrong with having multi-factor authentication on any account you have. Those people are as I personally see it the least in danger. But that is the setting that we are avoiding to look at. As I have said (way too often) that nonrepudiation is the way to go is showing to be the correct setting yet again.
Have a great day all, only 11 hours until Friday, or in Hobbit terms Frododay, the day you have two breakfasts and three lunches until the beer o clock chimes.